Amazon Web Services (AWS) has established itself as one of the most comprehensive cloud computing platforms, offering an array of services that cater to diverse workloads and operational needs. Among the many features AWS offers, VPC (Virtual Private Cloud) Interface Endpoints play a pivotal role in securely connecting to various AWS services without traversing the public internet. In this post, we’ll explore the purpose of AWS Interface Endpoints, their benefits, and specific use cases to help you understand when and why you should consider using them.
What Are AWS Interface Endpoints?
An AWS Interface Endpoint is a type of VPC endpoint that allows private connectivity between your VPC and AWS services. Instead of routing your traffic through the public internet, Interface Endpoints use AWS PrivateLink, a technology that enables the secure connection to AWS services from your VPC using private IP addresses.
So you might be asking why anyone would use a public endpoint for connecting to an AWS service like S3 or API Gateway. But these services, and many like them, deploy with public endpoints. Anytime you connect to one of these services using the default endpoint, it will traverse the public internet.
When you set up an Interface Endpoint, it creates an elastic network interface (ENI) within a specific subnet in your VPC. This ENI has a private IP address that serves as the entry point to access the service from within your private network. With Interface Endpoints, AWS services such as S3, DynamoDB, and others can be accessed securely without needing to go through the internet or modify your firewall rules to allow public IPs.
Purpose of AWS Interface Endpoints
The primary purpose is to offer secure, private access to AWS services. Let’s break this down further:
1. Private Connectivity:
The main goal is to enable communication between your VPC and AWS services without using the internet. By creating an endpoint inside your VPC, you ensure that data does not leave the secure boundaries of AWS’s private network. This reduces your network’s exposure to potential attacks or vulnerabilities associated with public internet traffic.
2. Simplified Network Architecture:
Without Interface Endpoints, connecting to AWS services typically requires an Internet Gateway (IGW) or NAT Gateway in your VPC. Interface Endpoints simplify this setup by allowing traffic directly from your VPC’s private subnets to AWS services without additional network components.
3. Reduced Latency and Improved Performance:
Since traffic stays within the AWS network and does not travel over the internet, Interface Endpoints can reduce latency and improve performance, especially for services that involve frequent or large data transfers.
4. Enhanced Security and Compliance:
Many organizations have strict compliance requirements that necessitate keeping all communication within a private network, particularly for industries like healthcare, finance, and government. Interface Endpoints help meet these security and regulatory standards by eliminating the need to expose workloads to the public internet.
This internal routing also reduces the risk of performance degradation due to factors outside of AWS control, such as internet routing issues, ISP throttling, or cross-region internet traffic delays.
Additional Benefits of Using AWS Interface Endpoints
Now that we understand their purpose, let’s dive into some of the other benefits you get from using them:
1. Enhanced Security
Interface Endpoints provide private communication with AWS services, which means your data never traverses the public internet. This minimizes potential exposure to cyber threats, such as DDoS attacks, man-in-the-middle attacks, or data interception. All communication occurs over AWS’s internal network, making it inherently more secure than relying on internet-based traffic.
Additionally, because they are deployed within your VPC with an ENI, you can leverage security groups to further control and restrict access to these services. This gives you greater control over which resources within your VPC can communicate with AWS services, allowing for tight security policies.
2. Simplified Network Configuration
When using public AWS endpoints, you often need to configure an Internet Gateway or NAT Gateway to route traffic, which can complicate network setup. By using Interface Endpoints, you can bypass these extra configurations and have a streamlined, simplified architecture that reduces the complexity of your VPC setup.
Moreover, they eliminate the need for managing public IPs, firewall configurations, and internet-based networking, making your network configuration more straightforward.
3. Cost Efficiency
While NAT Gateways provide internet access for private subnets, they can incur significant costs, especially when handling high volumes of data. Interface Endpoints can be more cost-effective since they remove the need for NAT Gateway usage, helping to minimize overhead for internet-bound traffic.
Additionally, Interface Endpoints typically charge only for the data processed, which may be cheaper than NAT Gateway hourly costs, especially if your data volume is low or infrequent.
4. Ease of Management
They are highly manageable and scalable. They can be added to existing VPCs easily, allowing you to extend private connectivity to AWS services with minimal effort. You can also enable endpoint policies, which allow you to specify which VPC resources can access the services through the endpoint, providing granular control over access permissions.
When Should You Use AWS Interface Endpoints?
Knowing when to use is crucial for optimizing your AWS architecture. Here are a few scenarios where Interface Endpoints are highly beneficial:
1. For Enhanced Security and Compliance
If your organization deals with sensitive data that must comply with regulatory frameworks like HIPAA, PCI-DSS, or GDPR, using Interface Endpoints is highly recommended. Keeping all data traffic within AWS’s private network helps ensure compliance with strict security requirements.
For example, if you’re running a healthcare application that interacts with Amazon S3 for storing patient data, using an Interface Endpoint can ensure that none of this sensitive information is exposed to the public internet, thereby reducing the risk of data breaches.
2. Private Access to AWS Services
If you are operating within a private subnet without internet access and need to interact with AWS services (like accessing S3 buckets or invoking Lambda functions), an Interface Endpoint becomes essential. Instead of provisioning an Internet Gateway or NAT Gateway, you can use Interface Endpoints to privately access these services without opening up your subnet to public internet access.
3. Optimizing Network Latency
If your application is latency-sensitive or handles large volumes of data transfers, Interface Endpoints help improve performance by ensuring that the traffic remains within the AWS network, resulting in lower latency and higher throughput compared to routing through the internet.
4. Reducing Network Costs
In scenarios where your workloads require frequent or high-volume communication with AWS services, Interface Endpoints can lead to cost savings by removing the reliance on NAT Gateways. This is particularly useful in large-scale applications where the NAT Gateway’s hourly costs and per-GB data processing fees may add up over time.
5. Multi-Region or Hybrid Architectures
For applications that span multiple regions or involve hybrid cloud environments, Interface Endpoints allow for consistent, secure access to AWS services, even when private subnets in different regions need to communicate.
Gateway Endpoints vs Interface Endpoints
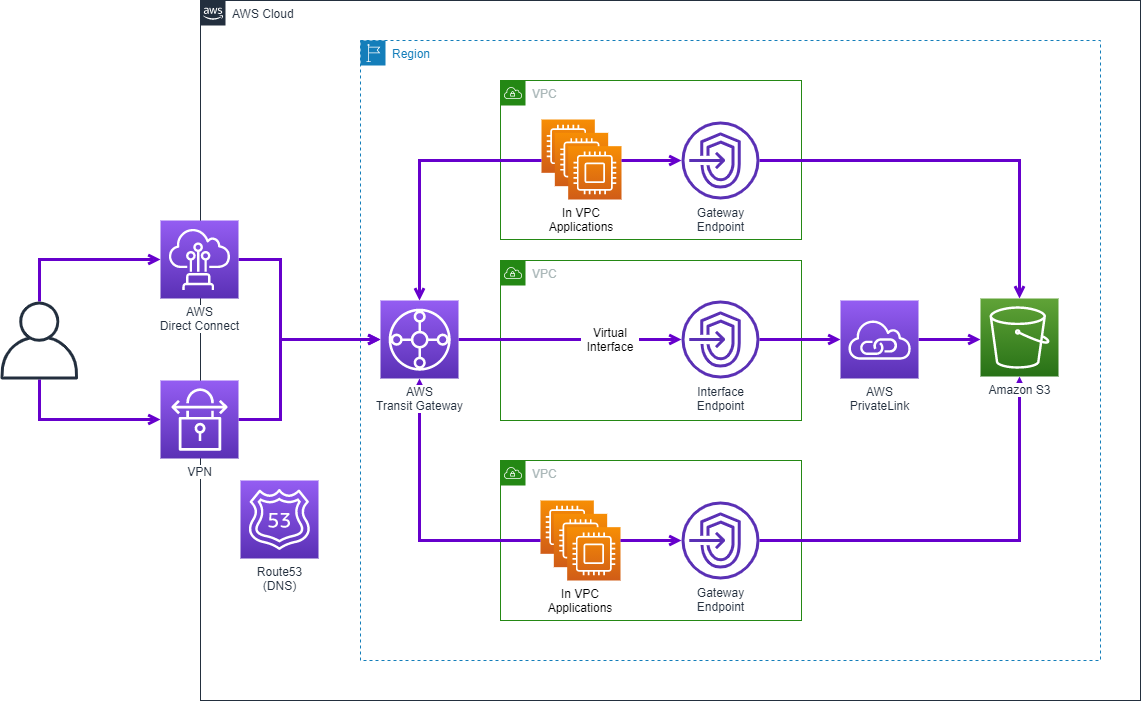
Throughout this post I’ve referenced Interface Endpoints to describe both types of endpoints that are available- Interface and Gateway. It’s important to distinguish between the two, so you select the one that’s most appropriate for your use case.
In AWS, both gateway endpoints and interface endpoints are used to enable private communication between your Virtual Private Cloud (VPC) and AWS services, without needing an Internet gateway, NAT device, VPN connection, or AWS Direct Connect. However, they differ in terms of their use cases, underlying implementation, and how they are configured:
Gateway Endpoint
A gateway endpoint is a target for a route in your route table used specifically for connecting to certain AWS services from within your private AWS network. Currently, gateway endpoints are available only for Amazon S3 and DynamoDB. Using gateway endpoints incurs no additional charges, but these are only for connecting to services from within your VPC’s.
Interface Endpoint
An interface endpoint is actually for requests from outside of your VPC, such as from on-prem. Interface endpoints support a wide range of AWS services, including S3, Dynamo DB, API Gateway, Lambda, Bedrock, STS, and many others. When an interface endpoint is created, it sets up a unique ENI in a specified subnet within your VPC. This ENI has a private IP address that your resources use to connect to the service privately. Interface endpoints come with an associated cost for data processing and hourly usage.
Conclusion
AWS Interface and Gateway Endpoints provide a powerful, secure, and efficient way to connect your VPC to AWS services. By leveraging PrivateLink, Interface Endpoints allow for private connectivity that enhances security, reduces complexity, and improves performance—all while helping to reduce costs. Understanding the right use cases for Interface and Gateway Endpoints can significantly improve your cloud infrastructure’s efficiency, especially when working with sensitive workloads or latency-sensitive applications.
One final note- I have heard from sources within AWS that eventually Gateway and Interface Endpoints will become one service. You will no longer have to choose between one or the other. No eta on that change as of today.




